Sometimes a low-tech approach can be useful.
While working on an SEO related project, I encountered a problem with Google’s recommended authorization standard (Oauth2) where authorization tokens for Google Analytics accounts were being invalidated after their first use. I got around this by developing a client from an open source PHP class that uses the less secure, but in my situation, more reliable “HTTP Auth” ClientLogin authorization method to access Google’s Analytics API.
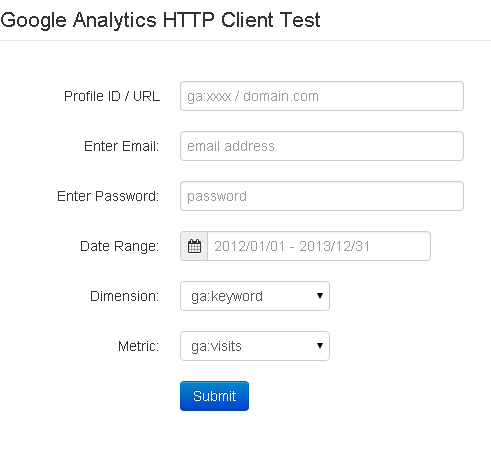
The client uses a direct HTTP authorization via Google credentials to log in to the Analytics account and then retrieves, via curl, and parses an XML feed based on RESTful style query. Please note that this is neither the most secure or recommended method of accessing Google’s API and there is no guarantee that they will continue to support the method with future API releases.
The attachment contains the PHP class and a test client for exploration. Feel free to modify and use as needed.
View the Google Analytics HTTP API at my github repository.
Users of software offered on this website, and those given permission for its use within software that they distribute, are bound by the following disclaimer of warranty:DISCLAIMER OF WARRANTY AND LIMITATION OF LIABILITY
THIS SOFTWARE IS FURNISHED “AS IS”. WITHOUT WARRANTIES, EXPRESS OR IMPLIED, THAT THE SOFTWARE IS FREE OF ERROR, OR IS CONSISTENT WITH ANY PARTICULAR STANDARD OF MERCHANTABILITY, OR THAT IT WILL MEET USER’S REQUIREMENTS FOR ANY PARTICULAR APPLICATION. I ACCEPT NO RESPONSIBILITY FOR ANY MATHEMATICAL OR TECHNICAL LIMITATIONS OF THE PROCEDURES AND FUNCTIONS WHICH MAKE UP THE SOFTWARE. WITHOUT ADDITIONAL THOROUGH TESTING BY USER, THE SOFTWARE SHOULD NOT BE RELIED ON FOR SOLVING A PROBLEM WHOSE INCORRECT SOLUTION COULD RESULT IN INJURY TO A PERSON OR LOSS OF PROPERTY. I SHALL NOT IN ANY EVENT BE LIABLE FOR ANY DAMAGES, WHETHER DIRECT OR INDIRECT, SPECIAL OR GENERAL, CONSEQUENTIAL OR INCIDENTAL, ARISING FROM USE OF THE SOFTWARE. USE OF THE SOFTWARE IS ENTIRELY AT USER’S OWN RISK.